Technology, finance, energy, healthcare, and government are just a few of the sectors that are racing to adopt cloud-based and containerized web apps.
There is no denying the advantages, but this change also brings with it new security risks.
According to OPSWAT’s 2023 study on web application security,
This year, 75% of businesses updated their infrastructure.
78% of them have raised their spending on security.
Only 2%, however, feel secure in their security posture.
Let’s examine why infrastructure upgrades lag behind faith in security and how OPSWAT bridges that divide.
Infrastructure Changes More Quickly Than Security Updates.
Security patch releases can’t keep up with the speed of technology development. The security of file uploads is where this disparity is most noticeable. Businesses are modernizing their infrastructure by adopting scalable, distributed apps that make use of cloud services and microservices, opening up new attack vectors for cybercriminals.
Cloud Storage #
Because of the efficiency and scalability of public cloud hosting, businesses are shifting to it. While private clouds and on-site hosting are declining, Software as a Service (SaaS) is becoming more and more popular. Data is dispersed among several cloud storage companies. Regrettably, this introduces more attack avenues and complexity.
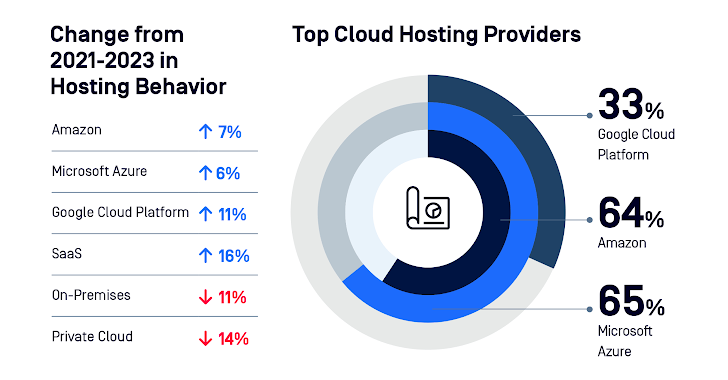
Companies Are Moving Towards Containers #
In their web hosting setups, 97% of enterprises utilize containers or plan to implement them over the course of a year. Docker, AWS Kubernetes, and Azure Kubernetes are excellent options. File upload attacks that take advantage of obsolete and insecure components are made possible by misconfiguration and the growing need for upgrades for microservices.
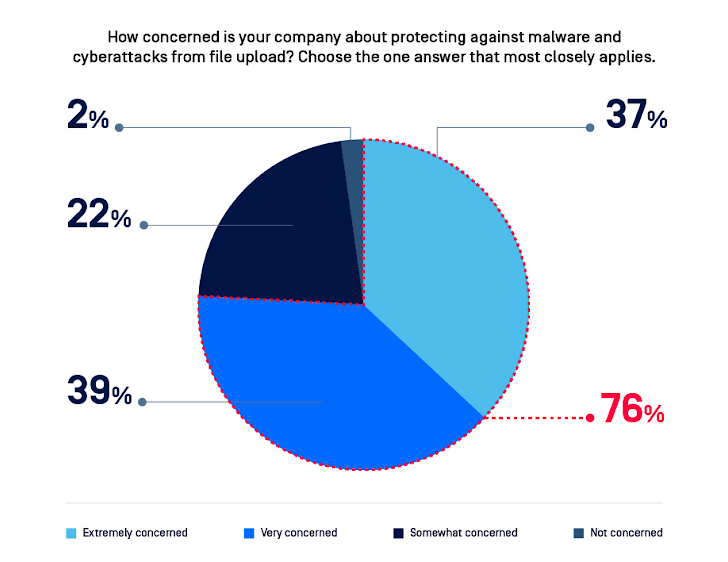
Concern#: Unsecure File Uploads
According to our survey, there are three main concerns:
Data Violations#
Security breaches are the main worry. Regulatory fines, loss of revenue or business, and reputational harm complete the list. Cybercriminals have access to private information, which can result in monetary losses, fines from the government, and reputational harm.
Compliance #
With the largest percentage of responders, the General Data Protection Regulation (GDPR) is in the lead. It was a motivating element for 56% of firms when making security decisions.
Malware: 98% of those surveyed are worried about file upload-related malware threats.
To arrange a 15-minute demonstration of how OPSWAT can protect your web applications against malicious file uploads, click this link.
File Upload Security Issues Must Be Fixed
More and more, businesses are moving their operations to cloud hosting and containerized web apps, which makes security measures even more important. This is particularly true when allowing file uploads, since file upload flaws allow hackers to gain access to secure networks.
We discovered:
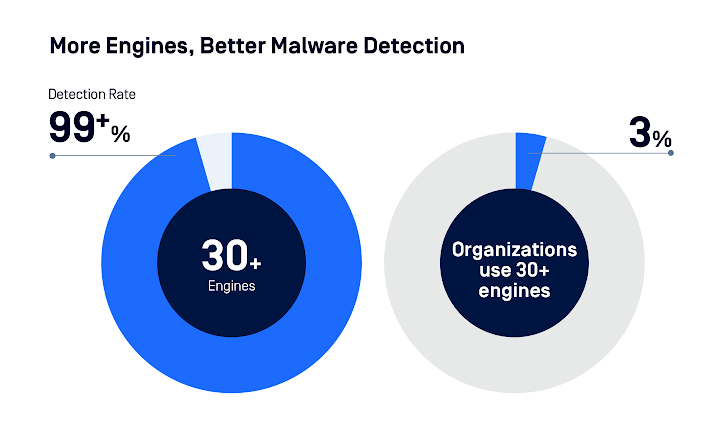
Just 63% of people scan for malware using several engines.
Merely 32% of files are disarmed using Content Disarm and Reconstruction (CDR) in order to address embedded and zero-day threats.
It is essential to use multiple anti-malware engines. Over 30 engines were scanned, and the accuracy rate was over 99%.
The Way Ahead#
Employing prevention- and detection-based technologies, enterprises require an integrated solution to stay up with the rapidly changing infrastructure and growing attack surface.
Additional Antivirus Engines
In order to protect against malicious file uploads and malware, using multiple antivirus (AV) engines can boost detection rates and add extra levels of security. Every antivirus engine has an own set of guidelines and formulas for identifying a variety of dangers.
#Deep CDR
Disarms Active Content & Regenerates Safe Files # According to our survey, big businesses use Deep CDR to disarm content that is considered potentially dangerous and to regenerate safe files. It also alerts users to and blocks files that are outside of policy and contain embedded objects, like JavaScript in PDFs or macros.

One Billion Information Points
Maintaining web apps free of vulnerabilities is essential. In order to stop hackers from exploiting future backdoors, it is strongly advised that businesses use File-Based Vulnerability Assessment technologies to find and fix application and file-based vulnerabilities prior to installation. Utilizing our proprietary technology (U.S. 9749349 B1), we evaluate vulnerabilities gathered from more than one billion data points of individuals and devices operating in the wild.
AI-Powered Malware Identification #
In order to identify zero-day malware and locate Indicators of Compromise (IOCS) from a variety of sources, including files and URLs, OPSWAT Filescan rapidly performs fast adaptive threat analysis on files. To conduct in-depth analysis, it makes use of machine learning-powered fuzzy hashing and similarity scores.
A Billion Data Points #Result #
The attack surface increases when web application infrastructure moves to the cloud. The best course of action to prevent malicious file uploads and data loss is to use OPSWAT MetaDefender. By combining important file upload security solutions that work seamlessly with your existing infrastructure, you can stay up to date with the constantly changing threat landscape.
Are you prepared to see our file upload security solution in action? Speak with one of our security specialists right now.
wish to learn more from the Web Application Security Report for 2023.


